unlock LUKS with Dropbear SSH public key
Table of Contents
Updates
- Jan 25, 2026: updating the default config directory to
/etc/dropbear/initramfs/
image from https://mythicaustralia.com/drop-bear-size-chart/
How to unlock LUKS enabled disk on headless linux machine
N5105 PCB
I recently purchased this puppy and planned to use it as my home lab + router. I encrypted the entire disk with LUKS1 and wondered how to unlock it headlessly.
Dropbear SSH seems to be the optimal solution in this case. (Cuz we all love Aussie hoax :)))
About Dropbear
Dropbear’s webpage doesn’t really work atm (well it works as of Jan 2026), but luckily we had Dropbear SSH on archive.org:
Dropbear is a relatively small SSH server and client. It runs on a variety of unix platforms. Dropbear is open source software, distributed under a MIT-style license. Dropbear is particularly useful for “embedded”-type Linux (or other Unix) systems, such as wireless routers.
Features
- A small memory footprint suitable for memory-constrained environments – Dropbear can compile to a 110kB statically linked binary with uClibc on x86 (only minimal options selected)
- Dropbear server implements X11 forwarding, and authentication-agent forwarding for OpenSSH clients
- Can run from inetd or standalone
- Compatible with OpenSSH ~/.ssh/authorized_keys public key authentication
- The server, client, keygen, and key converter can be compiled into a single binary (like busybox)
- Features can easily be disabled when compiling to save space
- Multi-hop mode uses SSH TCP forwarding to tunnel through multiple SSH hosts in a single command. dbclient user1@hop1,user2@hop2,destination
Setup
The setup process is pretty straight forward.
- my setup:
❯ lsblk -o NAME,SIZE,TYPE,FSTYPE,MOUNTPOINT
NAME SIZE TYPE FSTYPE MOUNTPOINT
mmcblk0 116.5G disk
├─mmcblk0p1 512M part vfat /boot/efi
├─mmcblk0p2 488M part ext2 /boot
└─mmcblk0p3 115.5G part crypto_LUKS
└─mmcblk0p3_crypt 115.5G crypt LVM2_member
├─lab--vg-root 114.5G lvm ext4 /
└─lab--vg-swap_1 976M lvm swap [SWAP]
mmcblk0boot0 4M disk
mmcblk0boot1 4M disk
- to install dropbear SSH:
apt udpate && apt -y install dropbear-initramfs
- to configure dropbear SSH with public key authentication, edit
/etc/dropbear/initramfs/dropbear.conf, edit theDROPBEAR_OPTIONSfield:
DROPBEAR_OPTIONS="-I 240 -p <your-port> -s -g -j -k"
all options (click to expand)
❯ dropbear -h
Dropbear server v2020.81 https://matt.ucc.asn.au/dropbear/dropbear.html
Usage: dropbear [options]
-b bannerfile Display the contents of bannerfile before user login
(default: none)
-r keyfile Specify hostkeys (repeatable)
defaults:
- dss /etc/dropbear/dropbear_dss_host_key
- rsa /etc/dropbear/dropbear_rsa_host_key
- ecdsa /etc/dropbear/dropbear_ecdsa_host_key
- ed25519 /etc/dropbear/dropbear_ed25519_host_key
-R Create hostkeys as required
-F Don't fork into background
-E Log to stderr rather than syslog
-m Don't display the motd on login
-w Disallow root logins
-G Restrict logins to members of specified group
-s Disable password logins
-g Disable password logins for root
-B Allow blank password logins
-T Maximum authentication tries (default 10)
-j Disable local port forwarding
-k Disable remote port forwarding
-a Allow connections to forwarded ports from any host
-c command Force executed command
-p [address:]port
Listen on specified tcp port (and optionally address),
up to 10 can be specified
(default port is 22 if none specified)
-P PidFile Create pid file PidFile
(default /var/run/dropbear.pid)
-i Start for inetd
-W <receive_window_buffer> (default 24576, larger may be faster, max 1MB)
-K <keepalive> (0 is never, default 0, in seconds)
-I <idle_timeout> (0 is never, default 0, in seconds)
-V Version
place your public key into
/etc/dropbear/initramfs/authorized_keysand then runupdate-initramfs -uto update the existing initramfs.go ahead and reboot your system. you should now able to ssh into your system using
ssh root@<ip> -p <port> -i /path/to/private/key. Then use the commandcryptroot-unlockto unlock the disk.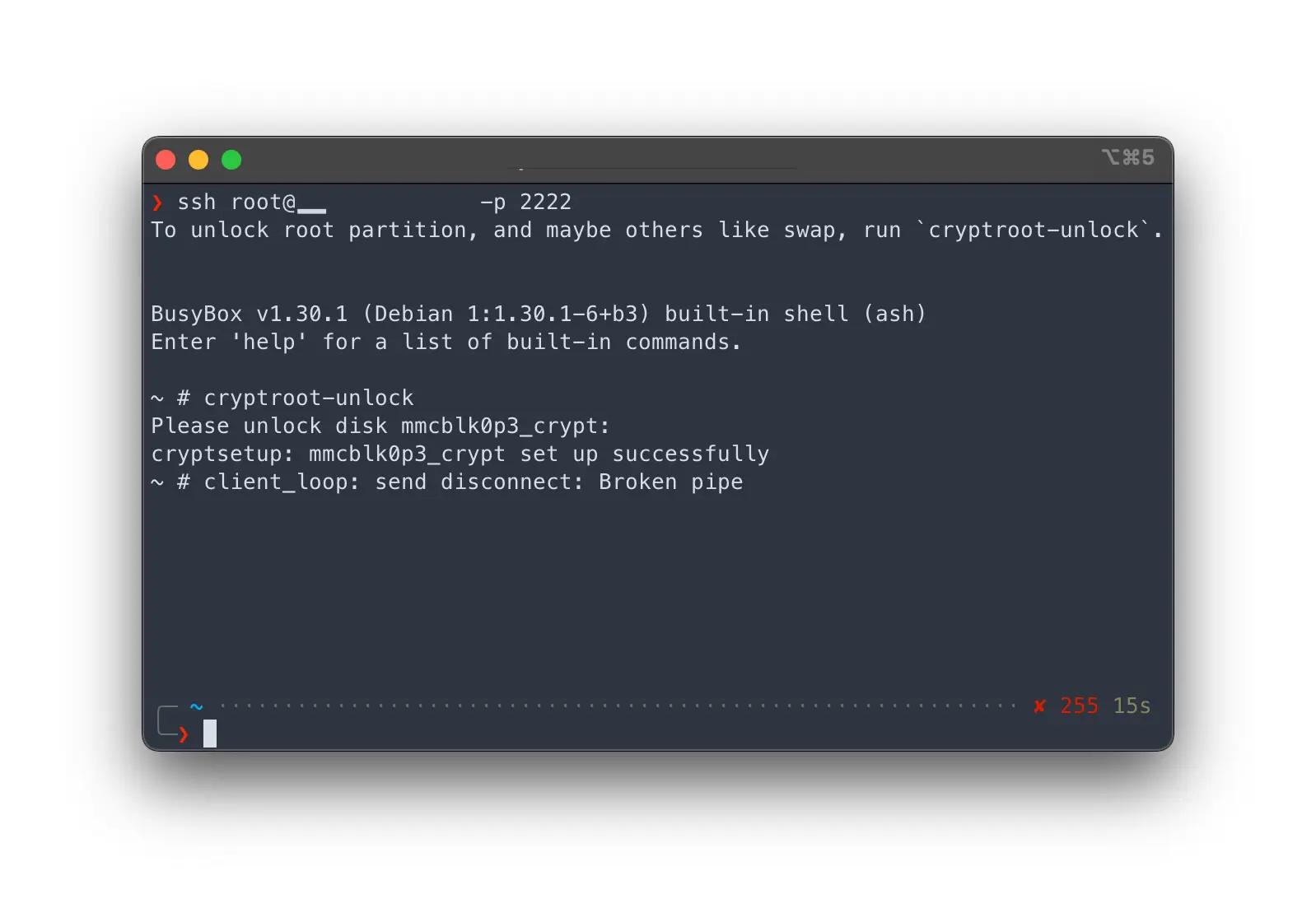
Hope you noticed that this is my first post with a cover image, cuz, again, we all love Aussie hoax. Don’t we?